The malicious assaults and Internet security threats for enterprise application can affect any website, whether a sizeable online bank handles millions of dollars in daily transactions or a shop for tiny local enterprises. An enterprise app development company has become an enormous responsibility to protect the app or website from cyber-attacks.
According to a new prediction by Forrester Analytics, application security solution spending is anticipated to increase to $7.1 billion by 2023, representing a 16.4% compound annual growth rate from 2017.
Hackers frequently select their victims based on their susceptibility rather than their scale or notoriety. Smaller systems, which may or may not include sensitive data, can be more appealing targets simply because they are easier to break.
Because the number of attacks has grown and data has become more personal and valuable, enterprise application cybersecurity has become increasingly crucial. Businesses cannot afford to ruin their brand even once in today’s relatively open and inclusive society.
Organizations, especially enterprise app development companies, should integrate cybersecurity considerations into the development phase of web applications to offer adequate protection against web application cybersecurity issues. Sadly, most developers put it off until the last possible moment.
This blog discusses the numerous areas of vulnerability that corporations must secure to avoid threats to enterprise application development and the alternative approaches that can be used.
Why enterprise application security matters
Customers conduct business online more often than ever. As companies undergo extensive digital transformations, corporate systems and software are becoming more complicated, blurring the lines between our real and digital worlds.
Security lapses can harm your brand’s reputation, undermine consumer confidence, and lower employee productivity. Security issues are becoming more prevalent, especially in the hybrid working period, where employees use their own devices and networks. Organizations should strengthen their security protocols to protect sensitive information, guarantee consumer privacy, and defend their intellectual property from cyberattacks, data theft, and ransomware.
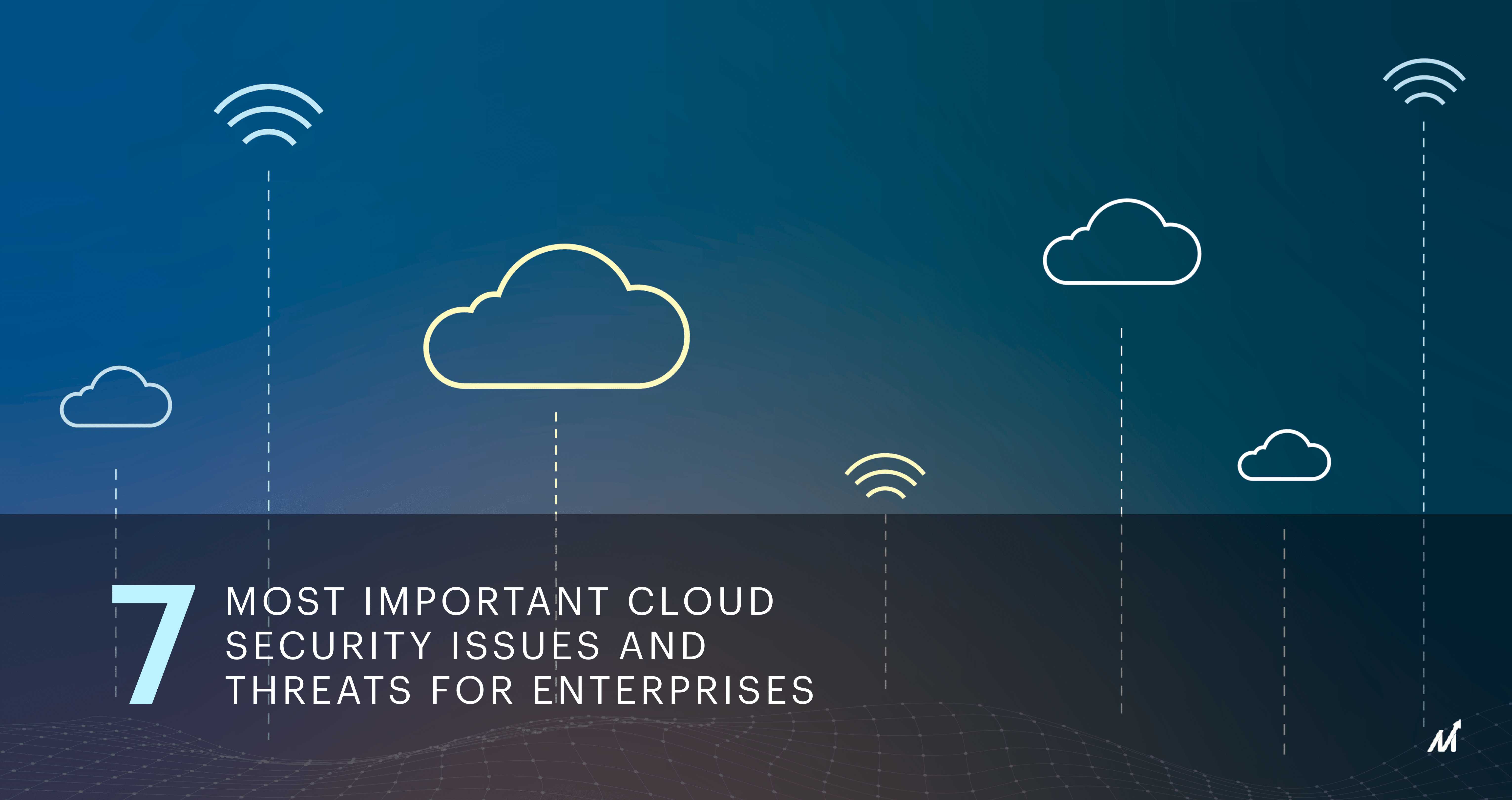
7 most crucial cloud security issues and threats for enterprise application
1. Brute force attack
In a brute force attack, the hacker tries many password possibilities in various permutations until one is successful (typically with the assistance of automation). Consider it is attempting every conceivable combination of numbers to unlock a combination padlock.
How to prevent:
- Several CMS and popular programs have software that analyzes your machine for recurring login failures or provides this information through a plugin system.
- These programs and plugins are the finest anti-brute-force defenses since they significantly limit the number of attempts that may be made.
- Make the root user inaccessible via SSH.
- Limit logins to a specified IP address or range.
2. Injection attacks
An injection-vulnerable web application takes anonymous data from an input field without sanitizing it. By entering code into an input field, the attacker can persuade the server to perceive it as a system command, leading the server to behave in the attacker’s favor.
SQL injections, Cross-Site Scripting, Email Header Injection, and other injection threats for enterprise application is expected. Unauthorized disclosure of databases and the leveraging of administrative access could be the result of these attacks.
How to prevent:
- Update any framework, CMS, or development platform with cybersecurity fixes regularly. When programming, use the best input sterilization procedures.
- All user input, no matter how minor, should be evaluated against a set of guidelines for what is anticipated.
- Several scripting languages provide built-in capabilities to sanitize input and ensure safe SQL execution to avoid SQL injections.
- Use these utilities to generate database queries using any variables.
3. Broken authentication
Broken authentication refers to a vulnerability in which encryption and essential control credentials have a wrong implementation. These can lead to cyber threats to enterprise applications.
Hackers can assert a valid user’s identity, access sensitive data, and potentially leverage the assigned ID privileges because of this incorrect implementation.
How to prevent:
- Wherever possible, use two-factor authentication to avoid cyber security threats for enterprise applications.
- Even if the hackers obtain or guess the correct password, this can safeguard a login.
- Also, update your passwords regularly (every 60 or 90 days, for example), and never use the same one multiple times.
- Implement multi-factor authentication (2FA/MFA).
4. Cross-site scripting (XSS)
It’s a client-side injection-based attack. At its essence, this attack injects malicious code into a website application for it to be executed on the victims’ web pages. Such threats to enterprise applications can affect any program that does not sufficiently check malicious files.
User session IDs are stolen, websites are defaced, and users are sent to fraudulent sites if the implementation is successful (thereby allowing phishing attacks).
How to prevent:
- Adjust your site’s comprehensive cloud security policies to limit the source URLs of remote modules and pictures to only your domain and any external URLs you need.
- This simple and quite often technique can stop many XSS attacks before they even start.
- Most XSS attacks rely on the site developer’s failure to take precautions.
- If you’re a coder, you can avoid these online security issues by appropriately escaping HTML tag characters, such as converting and > to and > on any user input JavaScript processes.
5. Sensitive data leak
When data leaks, like ransomware, happen, they usually make the news. Customer information or proprietary intellectual property, such as source code, might be exposed due to data leaks.
Hackers find interest in anything that is in hidden mode. This material is often well-protected, and compromise is usually achieved through other means, such as insider threats or social engineering.
How to prevent:
- Keep the confidential information hidden behind cyber network security and login limitations.
- Limit the number of people who have access. Ensure that all user access has solid passwords and, where possible, multi-factor authentication and that users update their passwords regularly.
- Consider adopting a secure, managed email platform to avoid phishing and harmful links.
- The developers should restrict physical access to critical systems as well.
6. Credential stuffing attack
Hackers that abuse the re-use of credentials across several accounts are now known as credential stuffers. If a hacker gets their hands on one of your account passwords, you can bet they’ll try to get into dozens of other popular services using the same login and password.
How to prevent:
- The most straightforward approach to avoiding this cyber security problem is never to use the same login or password for numerous services.
- Multi-factor verification also aims to mitigate this by securing the login even if one compromises the primary password.
- Limit authentication requests and set up failed request alerts.
- Use multi-factor authentication (MFA).
- Use a web application firewall (WAF).
7. Data breach
A data breach occurs when unknown individual access your personal information. They may not have a copy of the data or control it, but they can examine it and make modifications if necessary.
You might not even be aware of a breach right away. For example, the attacker may know the password to an administrative account but hasn’t utilized it to make any modifications.
How to prevent:
- This Cyber security problem might be difficult to solve since cyber attackers at this point are usually taking precautions to remain undetected.
- Several programs will print the connection details from your last session when you log in.
- When this information is available, be aware of it, and be cautious of unfamiliar activities.
- These notifications are available natively or through popular content management systems and open-source applications plugins. Other plugins automate checking your website’s files for new additions or changes.
- The more you use these tools, the better you’ll be able to spot any potentially questionable activities.
- You have the best alternatives for cleanup and prevention if you notice security vulnerabilities early.
Further Reading: The Best Technology Stack For Enterprise-level Application Development
Strategies to avoid threats to enterprise applications during the software development lifecycle (SDLC)
Introduce security guidelines and recommendations during the product development stage of the application. For example, Integrate penetration testing in the initial phases of development.
Secure programs in production environments by enforcing security processes and structures. For example, Carry out periodic security checks to ensure fewer cloud security risks.
Programs should use Robust authentication that contains sensitive information or are mission-critical.
Use firewalls, web application firewalls (WAF), and intrusion prevention systems (IPS) as surveillance systems.
How Markovate helps in securing enterprise applications while providing a seamless experience
While each vulnerability has a wide range of fixes, writing your code to protect an application from threats to enterprise application security is not particularly simple. It can be unscalable to manage an extensive portfolio.
It is generally better to rely on specialized digital security companies that have invested years of research into making security a deciding element when designing scalable programs.
Through a layered security environment, Markovate safeguards user identification. We are utilizing OpenID Connect, the APIs (OAuth 2.0 protocol). AWS and Microsoft Azure also host applications on Markovate.
The CIAM platform also makes sure that it is updated with the most recent regional compliances and governmental rules. The cloud directory manages and permits customer consent for data gathering and use while safeguarding private consumer information.
Among other features, Markovate offers:
- End-to-end SSL encryption safeguards data in transit from unauthorized access.
- For increased user protection, passwords can be hashed one way, even from database administrators.
- SSO solutions allow users to quickly access numerous online properties using a single set of credentials.
Conclusion
It’s a fool’s errand to guarantee 100 percent computer security and zero breaches against cyber attacks. The technological world is constantly changing, and change brings new threats to enterprise applications.
The Internet of Things (IoT) is becoming more commonplace in businesses worldwide, and with such high levels of connectivity, we expose ourselves to more digital dangers.
An enterprise app development company must recognize that security, like profit and client-level SLAs, is a strategic goal that the IT team must address as a KPI.
Security is a shared duty of the company and its personnel against cyber attacks. Finally, security entails ensuring safety and monitoring all systems so the company may adopt preemptive and quick-response measures.

I’m Rajeev Sharma, Co-Founder and CEO of Markovate, an innovative digital product development firm with a focus on AI and Machine Learning. With over a decade in the field, I’ve led key projects for major players like AT&T and IBM, specializing in mobile app development, UX design, and end-to-end product creation. Armed with a Bachelor’s Degree in Computer Science and Scrum Alliance certifications, I continue to drive technological excellence in today’s fast-paced digital landscape.